This is a script I use to enumerate hosts with the nmap scanning tool. Feed it a host/ip and base directory (under which another directory will be created to store enumeration data).
Something like:
./enum_host.sh 192.168.0.7 /data/nmap_data
You can also find this in my Gists at github at https://gist.github.com/ryan-wendel/2266751e23641ed0ff38fb7a2c3502cf
The entire script:
#!/bin/bash
HOST="$1"
BASE="$2"
SCAN_UDP="1"
GRAB_BANNERS="1"
TOP_TCP_PORTS="100"
TOP_UDP_PORTS="50"
TEMPLATE_NUM="2"
TCP_FILE="${BASE}/${HOST}/tcp_scan_${HOST}"
TCP_DEEP_FILE="${BASE}/${HOST}/tcp_scan_deep_${HOST}"
UDP_FILE="${BASE}/${HOST}/udp_scan_${HOST}"
#SCRIPT_DIR="/home/users/rwendel/tools/nmap/scripts"
SCRIPT_DIR="/usr/share/nmap/scripts"
#PERF_OPTIONS="-n --max-rtt-timeout 500ms --max-retries 3 --max-scan-delay 20ms"
#PERF_OPTIONS="-n -T${TEMPLATE_NUM} --max-rtt-timeout 350ms --max-retries 2"
PERF_OPTIONS="-n -T${TEMPLATE_NUM} --initial-rtt-timeout 500ms --min-rtt-timeout 100ms --max-rtt-timeout 1000ms --host-timeout 10m --scan-delay 100ms --max-scan-delay 500ms --max-retries 2"
print_help() {
echo "Usage: $(basename $0) <host/ip> <project directory>"
}
if [ -z "${HOST}" ]; then
echo "Error: Provide me a host/ip"
echo
print_help
exit 1
fi
if [ -z "${BASE}" ]; then
echo "Error: Provide me a directory to output to."
echo
print_help
exit 2
fi
if [ -z "${SCAN_UDP}" ]; then
echo "Error: Provide me with a zero or one to control UDP toggle."
echo
print_help
exit 3
fi
if [ -z "${GRAB_BANNERS}" ]; then
echo "Error: Provide me with a zero or one to control banner toggle."
echo
print_help
exit 4
fi
mkdir -p ${BASE}/${HOST}
if [ "$?" -ne "0" ]; then
echo "Error: File permissions issue"
exit 5
fi
if [ "${GRAB_BANNERS}" -gt "0" ]; then
mkdir -p ${BASE}/${HOST}/banners
fi
nmap -Pn -sT --top-ports ${TOP_TCP_PORTS} ${PERF_OPTIONS} ${HOST} -oA ${TCP_FILE}
if [ "${GRAB_BANNERS}" -gt "0" ]; then
grep open ${TCP_FILE}.nmap 2>/dev/null | grep -v -e 'Not shown' -e '^#' -e scanned | cut -d'/' -f1 | while read PORT; do
#printf "$(amap -b ${HOST} ${PORT})" > "${BASE}/${HOST}/banners/${PORT}_tcp_banner.txt"
nmap -Pn -sV -sT -p ${PORT} ${PERF_OPTIONS} --script=banner --script-args=banner.ports=${PORT} ${HOST} > "${BASE}/${HOST}/banners/${PORT}_tcp_banner.txt"
done
fi
if [ "${SCAN_UDP}" -gt "0" ]; then
nmap -n -Pn -sU --top-ports ${TOP_UDP_PORTS} ${PERF_OPTIONS} --open ${HOST} -oA ${UDP_FILE}
if [ "${GRAB_BANNERS}" -gt "0" ]; then
grep open ${UDP_FILE}.nmap 2>/dev/null | grep -v -e 'Not shown' -e '^#' -e scanned | cut -d'/' -f1 | while read PORT; do
nmap -Pn -sV -sU -p ${PORT} ${PERF_OPTIONS} --script=banner --script-args=banner.ports=${PORT} ${HOST} > "${BASE}/${HOST}/banners/${PORT}_udp_banner.txt"
#printf "$(amap -u -b ${HOST} ${PORT})" > "${BASE}/${HOST}/banners/${PORT}_udp_banner.txt"
done
fi
fi
PORTS=$(grep open ${TCP_FILE}.nmap 2>/dev/null | cut -d'/' -f1 | perl -pe 's|\n|,|g' | sed 's/,$//g')
if [ -n "${PORTS}" ]; then
nmap -A -Pn -sT -p ${PORTS} ${PERF_OPTIONS} ${HOST} -oA ${TCP_DEEP_FILE}
grep 'tcp.*open' ${TCP_DEEP_FILE}.nmap
fi
PORTS=$(grep 'open.*netbios' ${TCP_DEEP_FILE}.nmap 2>/dev/null | cut -d'/' -f1 | perl -pe 's|\n|,|g' | sed 's/,$//g')
if [ -n "${PORTS}" ]; then
mkdir -p ${BASE}/${HOST}/smb
enum4linux -a ${HOST} > ${BASE}/${HOST}/smb/enum_${HOST}.txt
echo "######################## OS Discovery" > ${BASE}/${HOST}/smb/smb_info_${HOST}.txt
nmap -Pn -p ${PORTS} --script=smb-os-discovery ${PERF_OPTIONS} ${HOST} >> ${BASE}/${HOST}/smb/smb_info_${HOST}.txt
echo "######################## Security Mode" >> ${BASE}/${HOST}/smb/smb_info_${HOST}.txt
nmap -Pn -p ${PORTS} --script=smb-security-mode ${PERF_OPTIONS} ${HOST} >> ${BASE}/${HOST}/smb/smb_info_${HOST}.txt
echo "######################## System Info" >> ${BASE}/${HOST}/smb/smb_info_${HOST}.txt
nmap -Pn -p ${PORTS} --script=smb-system-info ${PERF_OPTIONS} ${HOST} >> ${BASE}/${HOST}/smb/smb_info_${HOST}.txt
echo "######################## Domains" >> ${BASE}/${HOST}/smb/smb_info_${HOST}.txt
nmap -Pn -p ${PORTS} --script=smb-enum-domains ${PERF_OPTIONS} ${HOST} >> ${BASE}/${HOST}/smb/smb_info_${HOST}.txt
echo "######################## Shares" >> ${BASE}/${HOST}/smb/smb_info_${HOST}.txt
nmap -Pn -p ${PORTS} --script=smb-enum-shares ${PERF_OPTIONS} ${HOST} >> ${BASE}/${HOST}/smb/smb_info_${HOST}.txt
echo "######################## Users" >> ${BASE}/${HOST}/smb/smb_info_${HOST}.txt
nmap -Pn -p ${PORTS} --script=smb-enum-users ${PERF_OPTIONS} ${HOST} >> ${BASE}/${HOST}/smb/smb_info_${HOST}.txt
echo "######################## Groups" >> ${BASE}/${HOST}/smb/smb_info_${HOST}.txt
nmap -Pn -p ${PORTS} --script=smb-enum-groups ${PERF_OPTIONS} ${HOST} >> ${BASE}/${HOST}/smb/smb_info_${HOST}.txt
echo "######################## SMB ls" >> ${BASE}/${HOST}/smb/smb_info_${HOST}.txt
nmap -Pn -p ${PORTS} --script=smb-ls ${PERF_OPTIONS} ${HOST} >> ${BASE}/${HOST}/smb/smb_info_${HOST}.txt
echo "######################## SMB Enum " >> ${BASE}/${HOST}/smb/smb_info_${HOST}.txt
nmap -Pn -p ${PORTS} --script=smb-mbenum ${PERF_OPTIONS} ${HOST} >> ${BASE}/${HOST}/smb/smb_info_${HOST}.txt
echo "######################## SMB Vulns " >> ${BASE}/${HOST}/smb/smb_info_${HOST}.txt
nmap -Pn -p ${PORTS} --script=smb-vuln* ${PERF_OPTIONS} ${HOST} >> ${BASE}/${HOST}/smb/smb_info_${HOST}.txt
echo "######################## Samba Vulns " >> ${BASE}/${HOST}/smb/smb_info_${HOST}.txt
nmap -Pn -p ${PORTS} --script=samba-vuln* ${PERF_OPTIONS} ${HOST} >> ${BASE}/${HOST}/smb/smb_info_${HOST}.txt
fi
PORTS=$(grep 'open.*http' ${TCP_DEEP_FILE}.nmap 2>/dev/null | cut -d'/' -f1 | perl -pe 's|\n|,|g' | sed 's/,$//g')
if [ "${PORTS}" ]; then
mkdir -p ${BASE}/${HOST}/http
echo "######################## Cookie Flags" > ${BASE}/${HOST}/http/http_info_${HOST}.txt
nmap -Pn -p ${PORTS} --script=http-cookie-flags ${PERF_OPTIONS} ${HOST} >> ${BASE}/${HOST}/http/http_info_${HOST}.txt
echo "######################## CORS" >> ${BASE}/${HOST}/http/http_info_${HOST}.txt
nmap -Pn -p ${PORTS} --script=http-cors ${PERF_OPTIONS} ${HOST} >> ${BASE}/${HOST}/http/http_info_${HOST}.txt
echo "######################## Cross Domain Policy" >> ${BASE}/${HOST}/http/http_info_${HOST}.txt
nmap -Pn -p ${PORTS} --script=http-cross-domain-policy ${PERF_OPTIONS} ${HOST} >> ${BASE}/${HOST}/http/http_info_${HOST}.txt
echo "######################## Methods" >> ${BASE}/${HOST}/http/http_info_${HOST}.txt
nmap -Pn -p ${PORTS} --script=http-methods ${PERF_OPTIONS} ${HOST} >> ${BASE}/${HOST}/http/http_info_${HOST}.txt
echo "######################## Headers" >> ${BASE}/${HOST}/http/http_info_${HOST}.txt
nmap -Pn -p ${PORTS} --script=http-headers ${PERF_OPTIONS} ${HOST} >> ${BASE}/${HOST}/http/http_info_${HOST}.txt
echo "######################## Vulns" >> ${BASE}/${HOST}/http/http_info_${HOST}.txt
nmap -Pn -p ${PORTS} --script=http-vuln* ${PERF_OPTIONS} ${HOST} >> ${BASE}/${HOST}/http/http_info_${HOST}.txt
echo "######################## WAF Detect" >> ${BASE}/${HOST}/http/http_info_${HOST}.txt
nmap -Pn -p ${PORTS} --script=http-waf-detect ${PERF_OPTIONS} ${HOST} >> ${BASE}/${HOST}/http/http_info_${HOST}.txt
echo "######################## WAF Fingerprint" >> ${BASE}/${HOST}/http/http_info_${HOST}.txt
nmap -Pn -p ${PORTS} --script=http-waf-fingerprint ${PERF_OPTIONS} ${HOST} >> ${BASE}/${HOST}/http/http_info_${HOST}.txt
fi
PORTS=$(grep 'open.*ftp' ${TCP_DEEP_FILE}.nmap 2>/dev/null | cut -d'/' -f1 | perl -pe 's|\n|,|g' | sed 's/,$//g')
if [ "${PORTS}" ]; then
mkdir -p ${BASE}/${HOST}/ftp
nmap -Pn -p ${PORTS} --script=ftp-vuln* ${PERF_OPTIONS} ${HOST} > ${BASE}/${HOST}/ftp/vulns_ftp_${HOST}.txt
nmap -Pn -p ${PORTS} --script=ftp-*-backdoor ${PERF_OPTIONS} ${HOST} > ${BASE}/${HOST}/ftp/vulns_ftp_backdoor_${HOST}.txt
nmap -Pn -p ${PORTS} --script=ftp-anon ${PERF_OPTIONS} ${HOST} > ${BASE}/${HOST}/ftp/ftp_anon_${HOST}.txt
fi
PORTS=$(grep 'open.*smtp' ${TCP_DEEP_FILE}.nmap 2>/dev/null | cut -d'/' -f1 | perl -pe 's|\n|,|g' | sed 's/,$//g')
if [ "${PORTS}" ]; then
mkdir -p ${BASE}/${HOST}/smtp
nmap -Pn -p ${PORTS} --script=smtp-vuln* ${PERF_OPTIONS} ${HOST} > ${BASE}/${HOST}/smtp/vuln_smtp_${HOST}.txt
nmap -Pn -p ${PORTS} --script=smtp-open-relay ${PERF_OPTIONS} ${HOST} > ${BASE}/${HOST}/smtp/smtp_open_relay_${HOST}.txt
nmap -Pn -p ${PORTS} --script=smtp-enum-users ${PERF_OPTIONS} ${HOST} > ${BASE}/${HOST}/smtp/smtp_enum_users_${HOST}.txt
fi
# MySQL
PORTS=$(grep 'open.*mysql' ${TCP_DEEP_FILE}.nmap 2>/dev/null | cut -d'/' -f1 | perl -pe 's|\n|,|g' | sed 's/,$//g')
if [ "${PORTS}" ]; then
mkdir -p ${BASE}/${HOST}/mysql
nmap -Pn -p ${PORTS} --script=mysql-* ${PERF_OPTIONS} ${HOST} > ${BASE}/${HOST}/mysql/mysql_${HOST}.txt
fi
# SSH
PORTS=$(grep 'open.*ssh' ${TCP_DEEP_FILE}.nmap 2>/dev/null | cut -d'/' -f1 | perl -pe 's|\n|,|g' | sed 's/,$//g')
if [ "${PORTS}" ]; then
mkdir -p ${BASE}/${HOST}/ssh
nmap -Pn -p ${PORTS} --script=ssh* ${PERF_OPTIONS} ${HOST} > ${BASE}/${HOST}/ssh/ssh_${HOST}.txt
fi
I have the following lines set for external scanning. I’ve been running into issues with network security devices rate-limiting or hiding ports from me when trying to scan too fast.
TOP_TCP_PORTS="100"
TOP_UDP_PORTS="50"
TEMPLATE_NUM="2"
PERF_OPTIONS="-n -T${TEMPLATE_NUM} --initial-rtt-timeout 500ms --min-rtt-timeout 100ms --max-rtt-timeout 1000ms --host-timeout 10m --scan-delay 100ms --max-scan-delay 500ms --max-retries 2"
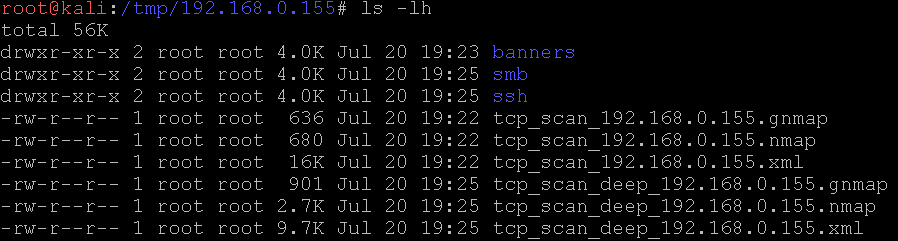
Which yields a directory that looks like.
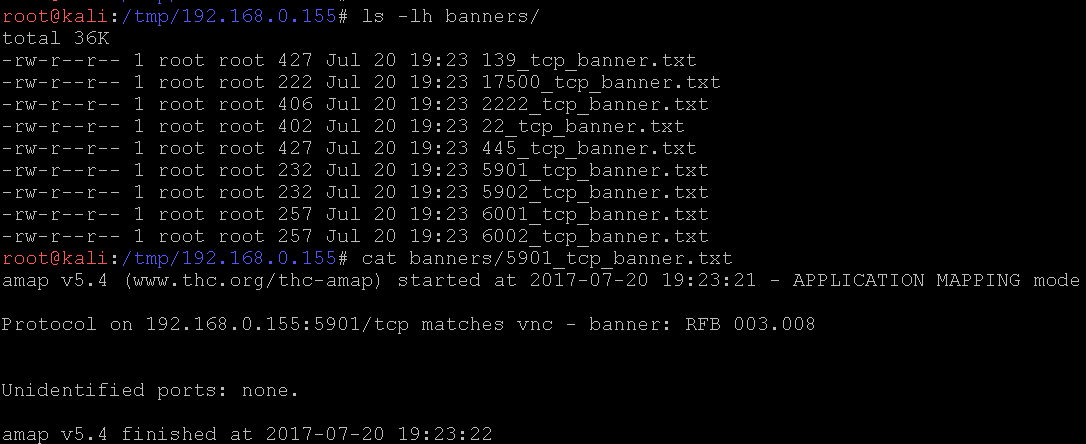
The banners directory.
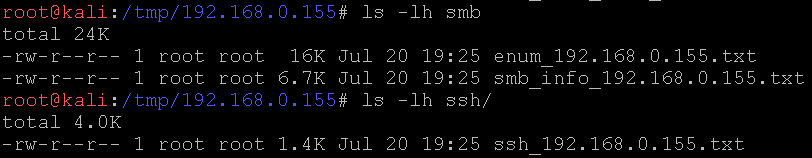
Various nmap nse script output, too. The enum file is enum4linux output. More work could be put into the service enumeration sections. I’ll get around to it at some point.